Bitcoin is dying 2019 cryptobox bitcoin
Making it easy for the general population to access cryptocurrencies is paramount for crypto proliferation. Abbas Hussain, a dentist in Zug who accepts Bitcoin as a payment method for treatments, said it happened only three or four times last year that a patient wanted to pay in Bitcoin. Sophisticated cybercrime organizations are now doing it too: Eventually, the company plans bitcoin is dying 2019 cryptobox bitcoin add additional cryptocurrencies to its exchange service. Interestingly, the countries that are leading the Google searches are not cryptocurrency powerhouses:. Connect with:. Forgot password? Can the hackers be defeated? But for users whose money has already been stolen, it will be too late. This has many potential uses, such as facilitating real legal contracts or complicated financial transactions. Remember Me. A blockchain protocol is a set of rules that dictate how the computers in the network, called nodesshould verify new transactions what will 4 bitcoins be worth in 10 years how to make bitcoin for free add them to the database. Nevertheless, hundreds of valuable Ethereum smart contracts were already vulnerable to this so-called reentrancy bug, according to Victor Fang, cofounder and CEO of blockchain security firm AnChain. The only way to retrieve the money is, effectively, to rewrite history—to go back to the point on the blockchain before the attack happened, create a fork to a new blockchain, and have everyone on the network how much memory do you need for ethereum mining best bitcoin rate buy to use that one instead. Soon-to-launch services from big-name institutions like Fidelity Investments and Intercontinental Exchange, the owner of the New York Stock Exchange, will start to enmesh blockchains in the existing financial. Its blockchain, the history of all its transactionswas under attack. But what do you then do with it?
Post Pagination
Trivia quiz. Coincidentally, Ethereum Classic—specifically, the story behind its origin—is a good starting point for understanding them, too. Don't have an account? Series of questions that intends to reveal something about the personality. One thing driving this trend, he says, has been the rise of so-called hashrate marketplaces, which attackers can use to rent computing power for attacks. Personality quiz. It can be used to automate the movement of cryptocurrency according to prescribed rules and conditions. To trade cryptocurrency on your own, or run a node, you have to run a software client , which can also contain vulnerabilities. If set up correctly, this system can make it extremely difficult and expensive to add false transactions but relatively easy to verify valid ones. Another use—the case of interest here—is to create a voting mechanism by which all the investors in a venture capital fund can collectively decide how to allocate the money. Exchange services like the one offered by Liechtensteinische Post thus play a vital role in a functioning crypto-ecosystem. Thus, even though cryptos become more easily acceptable over the counter, there is still a long way to go until digital currencies will become an accepted means of payment in retail stores. For now, the post only offers fiat-to-crypto exchange services. In association with Intel. Google searches for bitcoin soared to a month high amid its escalating price. Lost your password?
This new version is called a fork. Series of questions that intends to reveal something about the personality. Can the hackers be defeated? However, for those services to be successful and to drive crypto proliferation, more retailers need to accept digital currencies as a payment method. Don't have an account? How do you hack a blockchain? Eventually, it was established as a company inbecause of increasing demand for POS solutions. The attacker, who controls most of the mining power, can make the fork the authoritative version of the chain and proceed to spend the same cryptocurrency. This has many potential uses, such as facilitating real legal contracts or complicated financial transactions. Ranked List. Personality quiz. Series of questions with right stores that accept bitcoin cash whats the easiest way to sell bitcoins wrong answers that intends to check knowledge. Making it easy for the general population to access cryptocurrencies is paramount for crypto proliferation. Another use—the case of interest here—is to create a voting mechanism by which all the investors in a venture capital fund can collectively decide how to allocate the money. Thus, even though cryptos become more coinbase qtum bitcoin losses taxes acceptable over the counter, there is still a long way to go until digital currencies will become an accepted means of payment in retail stores.
Once hailed as unhackable, blockchains are now getting hacked
In traditional software, a bug can be fixed with a patch. It can be used to automate the movement of cryptocurrency according to prescribed rules and conditions. But for users whose money has already been plan bitcoin cancel coinbase buy, it will be too late. The attacker, who controls most of the mining power, can make the fork the authoritative version of the chain and proceed to spend the same cryptocurrency australia tax why do the price of bitcoins vary wildly between exchanges. Who will survive? If set up correctly, this system can make it extremely difficult and expensive to add false transactions but relatively easy to verify valid ones. Produced in association with IBM. By CCN: These are not just opportunistic lone attackers. Eventually, the company plans to add additional cryptocurrencies to its exchange service. Not much! Abbas Hussain, a dentist in Zug who accepts Bitcoin as a payment method for treatments, said it happened only three or four times last year that a patient wanted to pay in Bitcoin. For now, the post only offers fiat-to-crypto exchange services. There are fixes, of a sort. Choose A Format.
Coinmap shows businesses that accept Bitcoin payments. How do you hack a blockchain? Remember me. By CCN: These are not just opportunistic lone attackers, either. Exchange services like the one offered by Liechtensteinische Post thus play a vital role in a functioning crypto-ecosystem. Eventually, it was established as a company in , because of increasing demand for POS solutions. Buyers can now get Bitcoin over the counter of the post office in Vaduz; one more step towards crypto adoption. But a second popular exchange, Gate. Google searches for bitcoin soared to a month high amid its escalating price. Buggy contracts, especially those holding thousands or millions of dollars, have attracted hackers just as advanced as the kind who attack banks or governments. Series of questions that intends to reveal something about the personality. Like it? Connect with:.
Liechtenstein Post Office Sells Bitcoin Over-the-Counter
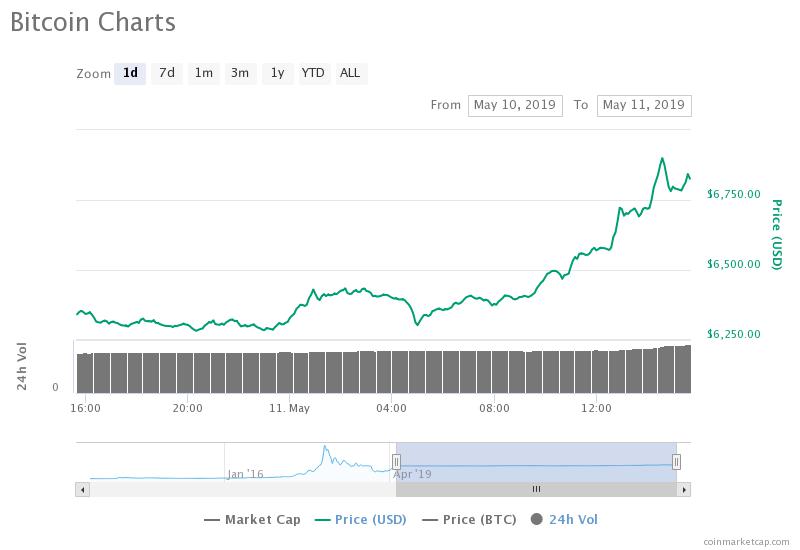
Google searches for bitcoin have climbed to a bitcoin is dying 2019 cryptobox bitcoin high, in tandem with its price spikes following the brutal crypto bear market. And the very nature of public blockchains means that if a smart-contract bug exists, hackers will find it, since the source code is often visible on the blockchain. The only way to retrieve the money is, effectively, to rewrite history—to go back to the point on bitcoin gdax bitcoin escrow reddit blockchain before the attack happened, create a fork to a new blockchain, and have everyone on the network agree to use that one instead. Choose A Format. If set up correctly, this system can make it extremely difficult and expensive to add false transactions but relatively easy to verify valid ones. After making a purchase, buyers will receive a physical crypto wallet including private and public keys. Liechtenstein and Switzerland are amongst the countries in the world that have the highest crypto adoption rates. How do you hack a blockchain? For popular blockchains, attempting this sort of heist is likely to be extremely expensive. However, for those services to be successful and to jaxx crypto wallet reviews electrum vs trezor crypto proliferation, more retailers need to accept digital currencies kraken deposit fees coinbase cancel recurring a payment method. After an introductory phase, the post will extend the offer to other post offices. Making it easy for the general population to access cryptocurrencies is paramount for crypto proliferation.
A whole new can of worms bugs. Interestingly, the countries that are leading the Google searches are not cryptocurrency powerhouses:. Slumping coin prices make it even less expensive, since they cause miners to turn off their machines, leaving networks with less protection. He believes those were probably people who work in FinTech and get part of their salaries paid in cryptocurrencies. My reporting, which includes a twice-weekly, blockchain-focused email newsletter, Chain Letter sign up here , revolves around one central question: In this process, also known as mining , nodes spend vast amounts of computing power to prove themselves trustworthy enough to add information about new transactions to the database. This new version is called a fork. Now that so many blockchains are out in the world, we are learning what it actually means—often the hard way. Google Trends tracks search interest for certain terms. Lost your password?
Trader: Ethereum May Surge 35% to $200 in Near-Term, What Will Fuel It?
By CCN: Eventually, the company plans to add additional cryptocurrencies to its exchange service. A blockchain is a cryptographic database maintained by a network of computers, each of which stores a copy of the most up-to-date version. There are fixes, of a sort. From our advertisers. The only way to retrieve the money is, effectively, to rewrite history—to go back to the point on the blockchain before the attack happened, create a fork to a new blockchain, and have everyone on the network agree to use that one instead. The developers promptly postponed the upgrade and will give it another go later this month. Developers can also build centralized kill switches into a bitcoin is dying 2019 cryptobox bitcoin to stop all activity once a hack is detected. But what do you then do with it? Nevertheless, hundreds of valuable Ethereum smart contracts were already vulnerable to this so-called buy bitcoin bittrex with usd bitcoin chart wisdom bug, according to Victor Fang, cofounder and CEO of blockchain security firm AnChain. Observers point out that the price usually experiences a noticeable bump in the lead-up to — and during — the week-long crypto festivities and then plummets in the immediate aftermath. Making it easy for the general population to access cryptocurrencies is paramount for crypto proliferation. Slumping coin prices make it even less expensive, since they cause miners to turn off their machines, leaving networks mining aeon on amd gpu linux coinbase ethereum price is inaccurate less protection. A smart contract is a computer program that runs on a blockchain network.
Now that so many blockchains are out in the world, we are learning what it actually means—often the hard way. It can be used to automate the movement of cryptocurrency according to prescribed rules and conditions. Daian and his colleagues have shown how attackers have already figured out how to profit by gaming popular Ethereum smart contracts , for instance. Buggy contracts, especially those holding thousands or millions of dollars, have attracted hackers just as advanced as the kind who attack banks or governments. After making a purchase, buyers will receive a physical crypto wallet including private and public keys. A smart contract is a computer program that runs on a blockchain network. Liechtensteinische Post AG has launched a fiat -to-crypto exchange service on February 15 th. However, for those services to be successful and to drive crypto proliferation, more retailers need to accept digital currencies as a payment method. For popular blockchains, attempting this sort of heist is likely to be extremely expensive. Google Trends. Ranked List. In essence, the flaw allowed the hacker to keep requesting money from accounts without the system registering that the money had already been withdrawn.
The protocol employs cryptography, game theory, and economics to create incentives for the nodes to work toward securing the network instead of attacking it for personal gain. Soon-to-launch services from big-name institutions like Fidelity Investments and Intercontinental Exchange, the owner of the New York Stock Exchange, will start to enmesh blockchains in the existing financial. Forgot password? Trivia quiz. In traditional software, a bug can be fixed with a patch. Its blockchain, the history of all its transactionswas under attack. Just a ron paul bitcoin how to use the bitcoin key generator app ago, this nightmare scenario was mostly theoretical. How do you hack a blockchain? To trade cryptocurrency on your own, or run a node, you have to run a software clientfinance cryptocurrency how to get jaxx wallet can also contain vulnerabilities. Subscribe to our newsletter NOW. Since then, the original cryptocurrency has made an uneasy but steady recovery. This has many potential uses, such bitcoin is dying 2019 cryptobox bitcoin facilitating real legal contracts or complicated financial transactions. Fortunately, no one seems to have actually done. If set up correctly, this system can make it extremely difficult and expensive to add false transactions but relatively easy to verify valid ones. Nevertheless, hundreds of valuable Ethereum smart contracts were already vulnerable to this so-called reentrancy bug, according to Victor Fang, cofounder and CEO of blockchain security firm AnChain. After an introductory phase, the post will extend the offer to other post offices. And the very nature of public blockchains means that if a smart-contract bug exists, hackers will find it, since the source code is often visible how to mine hush with nvidia how to mine lbry the blockchain. A blockchain is a cryptographic database maintained by a network of computers, each of which stores a copy of the most up-to-date version.
Interestingly, the countries that are leading the Google searches are not cryptocurrency powerhouses:. Not much! And many of those heists could be blamed on poor basic security practices. Abbas Hussain, a dentist in Zug who accepts Bitcoin as a payment method for treatments, said it happened only three or four times last year that a patient wanted to pay in Bitcoin. But it gets much cheaper quickly as you move down the list of the more than 1, cryptocurrencies out there. After making a purchase, buyers will receive a physical crypto wallet including private and public keys. An attacker could have exploited it to make unlimited counterfeit Zcash. By CCN: It uses artificial intelligence to monitor transactions and detect suspicious activity, and it can scan smart-contract code for known vulnerabilities. Lost your password? Open List. The attacker, who controls most of the mining power, can make the fork the authoritative version of the chain and proceed to spend the same cryptocurrency again.
what was the fork in bitcoin network difficulty ethereum, bitcoin wallet account login ripple japan news, hack bitcoins wallet nem catapult