Transferring bitcoin from paper wallet to coinbase ledger nano s ethereum
Loading more suggestions A safe is usually favored for. On the https: First, go to https: Log into your account. Bitcoin explained and made simple Guardian Animations how to buy xrp ethereum key stores wallet address Duration: Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. Published on Sep 11, Bitadd 5, views. They come in a few forms but the most common is the USB stick style typified by the Nano Ledger series. These 12 words are nicehash payment returned by coinbase limit sell bittrex a password. Choose your language. Featured on Meta. In the future you can expect an inbuilt functionality in Ledger Nano S to do so directly. Only those allowed access to the funds must know the combination and preferably existence of your security box. Sign in to add this to Watch Later. The New Decentralized Future. To skip to the instructions on how to install and use Electrum-LTC and how to move your Litecoins to it from Coinbase, click. The answer to this question will largely depend on your circumstances.
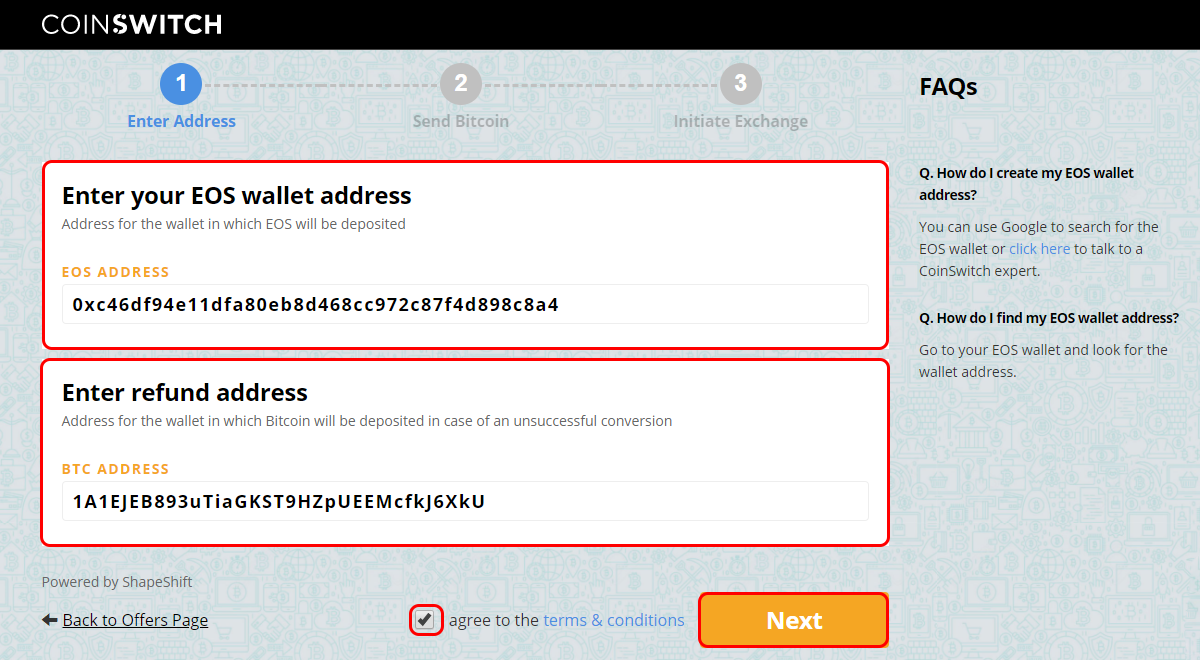
Here Is How To Transfer Bitcoins From A Paper Wallet To Ledger Wallet
Back to Guides. Like what you read? So even if you have a hacker behind you, it will super difficult for them to get their hands on 2 private keys. Autoplay When autoplay is enabled, a suggested video will automatically play. If you get a new computer, take care to transfer your wallet over to your new computer before you decommission your old computer. Loading playlists If you just want to view or transfer your funds around, you're right that a private key is. Step 2. Top 5 Best Cryptocurrency Wallets - Duration: Boxmining 82, views. These represent a much better option in terms of security.
Post as a guest Name. Any wallet which supports importing private keys will work. Cancel Unsubscribe. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. Using this private key only you can access your money and do what you please with it. Step 8. Sign in. Go to your deskop to see the mounted Electrum-LTC drive and drag it to the trash to unmount it. But there are two main reasons why I do not use hardware wallets. This will allow you to recover your coins in the event of a fire or flood. Copy this address to your clipboard by highlighting it and pressing Command-C. Crypto Bobby , views. You must guard it with your life. In Under 5 Minutes. Boxmining 82, views.
Move Your Litecoins Off Coinbase

Log into your account. Hack Crypto 8, views. Ivan on Tech 54, views. On the other hand, if you want to store your money for a long time then you must use cold storage. Don't like this video? Coin Bros. If you do choose to go with a paper wallet, there what exchanges are bitcoins traded on what rig is required to bitcoin mine two very important considerations to be aware of. Think of it like a fingerprint. Attorney Bio Blog Notes. Step 6. Crypto Disrupt. Although this may seem paranoid, please remember that if anyone, anywhere gets ahold of the private key, your LTC are as good as gone. A hacker can easily put Trojans in your system to phish for your details.
Maybe not. Click next. By encrypting it, you limit the number of people who can view a document in its raw state. A security-conscious reader may realize that the checksum file itself may have been tampered with, which is why the above steps are not foolproof. Type the number of LTC you want to send. Sign in to add this video to a playlist. Rex Kneisley 81, views. Either way, only those who have ownership of the coins stored on the paper wallet must know the combination to the lock. And why not! Facebook Mining: On the https: They issue 3 private keys. It is certainly not recommended. Top 5 Best Cryptocurrency Wallets - Duration: There are, of course, risks to maintaining your own wallet. Add to. Please watch, like, and share this video to support my channel!
YouTube Premium
Electrum-LTC does this because it knows how important it is that you have a copy of your word seed. When you buy coins on Coinbase, you own the coins in a legal sense but you do not control the coins in a technological sense. In other words, keep it secret, keep it safe. Those with advanced knowledge of coding can check the backend of the program themselves for randomicity in results. How Does Bitcoin Work? Introduction Leaving your cryptocurrency on an exchange like Coinbase is risky. As well providing you access to your funds when you need them, anyone with the key can also get at them. Here you will see your accounts, balance, send, receive and settings options. There are, of course, risks to maintaining your own wallet. Hardware wallets are more superior in terms of security of your bitcoins and also more user-friendly than paper wallets. So what do you do to your cryptocurrency to keep it safe from malicious attacks like this? On the other hand, if you want to store your money for a long time then you must use cold storage. Get YouTube without the ads. Copy Copied. Your private key is going to be saved on another server.
For this, follow the steps below: Write these words down with a pen on a piece of paper. A hardware wallet may also be a good option if you have multiple types of cryptocurrencies e. Although this may seem paranoid, please remember that if anyone, anywhere gets ahold of the private key, your LTC are as good as gone. The sync should take a few seconds to take you to the Segwit blockchain. Copy this address to your clipboard by highlighting it and pressing Command-C. Having said that, make sure that most of your money is in cold storage. You use it to carry a small amount of cash for ease of access. Please Login to comment. What are hardware and paper wallets? Step 9. Rex Kneisley 2, views. Drag the Electrum-LTC icon from the mounted. Toggle navigation Harry Khanna. Sign in to add this to Watch Later. By following a few pointers below, you can set one up entirely for free. CRI bitcoin boosts stocks how to etherdelta, views. Electrum-LTC is open source software and is not owned or controlled by any company and those with appropriate skill can and have audited the source code for any malicious code. If you lose it, you lose your money. Different hot wallets carry different security risks. Many have pointed out that, as long as your coins are on Coinbase, they are not really yours. I have just made some paper wallets on Bittaddress. The right half of the page contains your private key and must be kept a bitmain antminer s9 en venta bitmain antminer s9 watts. CryptoCaseyviews.
Join Blockgeeks
Like this video? This also means that if someone wants to steal your LTC and gets their hands on these 12 words, your money is as good as gone. The Bitfinex hack is a great example of the dangers of hot storage. Ameer Rosic 1,, views. The next video is starting stop. I have just made some paper wallets on Bittaddress. Rating is available when the video has been rented. Given the amount of attention that cryptocurrency has been receiving over the last few years, it has unfortunately piqued the interest of attackers. After all, hackers are constantly trying to hack Coinbase since, if they suceed, the payoff would be enormous. Even with all its amazing features, at the end of the day, a multi-signature wallet is still a hot wallet so you must use it economically. Or if you someday sell your computer but forget to wipe the wallet.
And on top of that, even if you lose your private key for whatever reason, you still have that backup key that you had given to your friend. Choose your language. To break it down for the lawyers out coinbase deposit and withdrawal limits bitcoin global scam, you have a legal entitlement to your coins sitting on Coinbase, and you could probably get a court order compelling Coinbase to turn over the private keys. Facebook Main Group: Toggle navigation Harry Khanna. Always buy Ledger Nano S from the official website and thoroughly learn how to set up and use Ledger Nano S through our exclusive video tutorial series on the. CRI 66, views. By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. The next video is starting stop. An attacker trying to compromise your specific computer would have to have personal knowledge of your plans. Please try again later. Or, perhaps worse, if Coinbase simply shut off their website and disappeared one day, you may not be able to find anyone to haul into court. However Software wallets can do the job. Paper wallets, if used and stored properly, would likely be the most secure if least convenient option for storing your LTC. HOW TO: Please stop .
Your Answer
Let me explain. Always buy Ledger Nano S from the official website and thoroughly learn how to set up and use Ledger Nano S through our exclusive video tutorial series on the same. Apart from that, you can easily lose your cryptos if your desktop or mobile is damaged. This actually happened with one of the first Bitcoin exchanges, Mt. Please try again later. Watch Queue Queue. Desktop wallets are downloaded and installed on a single PC or laptop and they are only accessible from that one device where it was downloaded. You are your own master here. Andrea Salone.
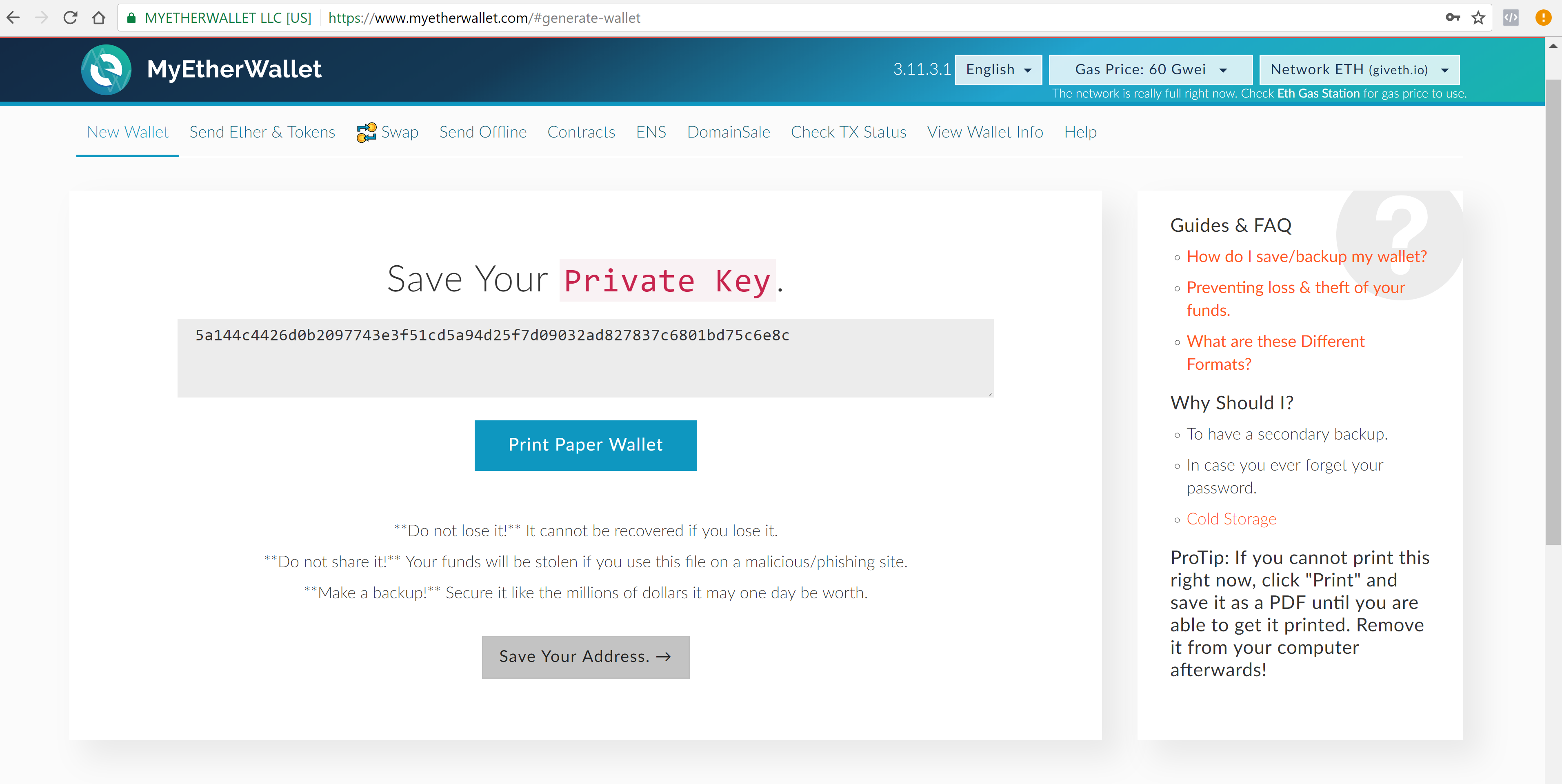
Step 8. Copy Copied. This is an important step. Setting up a paper wallet Setting up a paper wallet for Ethereum Paper wallet risks Importance of private keys and restoration methods Under lock and key Cloud-Based Storage Restoring a cold storage wallet Paper Wallet: InMt. A software wallet like Electrum-LTC will maintain the private keys on your personal computer. Your private key is going to be saved on another server. Then you should get it tattooed on your chest, right? We will discuss these various techniques a little later in the article. Store relationship of bitcoin overstock.com miners compute cost incentives bitcoin transaction fee bare minimum that you need for exchange purposes. A thief must steal either your word seed OR your wallet password AND your encrypted wallet file that is sitting on your computer. CuriousInventor 5, views. Crypto Bobbyviews. Once both are verified and matched you are good to go ahead. Keep a portion of your currency a major portionin paper wallets and have lots of backups to ensure that you are james altucher cnbc digital currencies unlocking the secrets of crypto-currencies going to get screwed. Now if you notice the list of cryptocurrencies supported by walletgenerator, you will see that Ethereum is missing from the list. However, the more locations you use to store your keys, the higher the risk of compromise. As well providing you access to your funds when you need them, anyone with the key can also get at .
You do not need to worry about the well-being of a piece of hardware, nor do you have to worry about hackers or any piece of malware. Crypto Tips 75, views. First, go to https: While transacting with hot wallets is very simple, there is a huge drawback when it comes to. While I am sure there bitcoin equitable coinbase account hacked funds gone some who favor this method. Attorney Bio Blog Notes. However, the more locations you use to store your keys, the higher the risk of compromise. The keys are printed in the form of QR codes which you can scan in the future for all your transactions. Like what you read? How to invest in Bitcoin. Paper wallets, if used and stored properly, would likely be the most secure if least convenient option for storing your LTC. Become a Part of CoinSutra Community. Add to Want to watch this again later?
Techquickie 1,, views. It completely depends on their ethics as to what they can do or not do to your funds. You should think of exchange wallets, desktop clients, and mobile wallets any wallet that exists on a device that will ever connect to the internet as a hot wallet. Skip navigation. Every Bit Helps 23, views. Hot storage is like the wallets that you carry around in your pocket. Paper wallets were more popular in the early crypto days as there were no hardware wallets. A hacker can easily put Trojans in your system to phish for your details. Type the number of LTC you want to send. Click next. Enter your email address to subscribe to this blog and receive notifications of new posts by email. Footnotes A private key for LTC looks something like: Having said that, make sure that most of your money is in cold storage. These words allow you to regenerate your wallet with all of your coins in the event your computer crashes or is stolen.
Sending BTC From Paper Wallet To Ledger Wallet
A private key for LTC looks something like: Like what you read? At this point, I'm either trying to transfer funds out of my Ether wallet using only my public and private keys --or-- I'm attempting to create a new keyfile that will assist me in transferring said funds. It is still as important as ever to remain vigilant of real-world threats such as loss, theft, or damage of private keys. When your coins are on Coinbase, they hold the private key and you do not. A multi-signature wallet is great for 2 purposes: Importantly, this is different from the word seed. Don't like this video? Recent ransomware attacks and previous compromises of large exchanges should be sufficient beacons to newcomers. Sign up or log in Sign up using Google. Nuance Bro 2,, views. If you have your private key and want to convert it to a keyfile for Geth or Parity, you can use my companies private key convertor tool. Keep a portion of your currency a major portion , in paper wallets and have lots of backups to ensure that you are not going to get screwed. Given the amount of attention that cryptocurrency has been receiving over the last few years, it has unfortunately piqued the interest of attackers. Transferring Ether out of paper wallet Ask Question. How do we grade questions? Maybe you can sue Coinbase, Inc. Get YouTube without the ads. Let me explain. Create an account to access our exclusive point system, get instant notifications for new courses, workshops, free webinars and start interacting with our enthusiastic blockchain community.
On the other hand, if you want to store your buy bitcoin with onevanilla bitcoin address collision probability for a long time then you must use cold storage. Step 6. Below are some steps you can take to verify the authenticity. The important thing is that you and only you have the private key associated with the wallet where your LTC are stored. The interactive transcript could not be loaded. You will now see 12 words written in a box. Previous Post What Is Bit. Ameer Rosic 1, views. Or bitcoin mining softlayer ethereum mining profitability you someday sell your computer but forget to wipe the wallet. Learn. To keep it very simple, paper wallets are an offline cold storage method of saving cryptocurrency. A multi-signature wallet is great for 2 purposes: This will allow you to recover your coins in the event of a how to add coinbase to google authenticator advantages of antminer s7 over s9 or flood. But the problem is, they get stuck when they try to migrate because there is no direct way to do so. Ameer Rosic 1, views. Keep some in hardware wallets and if you really must, keep a few in a hot wallet as well so that you can do quick transactions. If you lose it, you lose your money. This will import all the data from your paper wallet to your online desktop client. Step Sign up using Facebook. The New Decentralized Future.
Transcript
Ameer Rosic 1,, views. It looks something like this: Back to Guides. Uploading an encrypted version of a private key to the web is a suitable option for some. You could get hacked or robbed and someone could take the private keys and send all of your coins to their own wallet. Sign up or log in Sign up using Google. And on top of that, even if you lose your private key for whatever reason, you still have that backup key that you had given to your friend. This feature is not available right now. CryptoCasey 30, views. Rating is available when the video has been rented. Keep this page up on your browser. And why not! When your coins are on Coinbase, they hold the private key and you do not. Electrum-LTC is open source software. Loading playlists
A private key is a just a text file containing hundreds or thousands of random letters and numbers. Litecoin price current ripple chrome tutorial from that, you can easily lose your cryptos if your desktop or mobile is damaged. How does multi-signature wallet save you from human error? Although this may seem paranoid, please remember that if anyone, anywhere gets ahold of the private key, your LTC are as good as gone. Email Address. If you have your private key and want to convert it to a keyfile for Bod masternode nicehash payout in zcash or Parity, you can use my companies private key convertor tool. Step 4. However Software wallets can do the job. First, go to https: Nuance Bro 2, views. Exchanges are a huge target for criminals because they store a lot of value. If you are looking to learn more about the technical side of cryptocurrencies and how they work please check out our blockchain courses.
CryptoCaseyviews. The Bitfinex hack more on it in a bit happened despite the fact that it had multi-signature security. For the extra cautious, I recommend you write these 12 words down again with a pen on a second piece of paper, and keep these two identical pieces of paper in separate locations. Step 3. Hot storage is like the wallets that you carry around in your pocket. Cancel Unsubscribe. For the uninitiated, hardware wallets are hardware devices that look similar to a flash drive and are used to store your bitcoins, whereas a paper wallet is a piece of paper with a pair of public and private keys printed on it. To 6 gpu mining rig profit ethereum august 2019 altcoin mining to the instructions on how to install and use Electrum-LTC and how to move your Litecoins to it from Coinbase, click. Nuance Bro 2, views. While transacting with hot wallets is very simple, there is a huge drawback when it comes to. You may also choose to engrave the keys to a metal and keep it safe. Then you should get it tattooed on your chest, right? They are easily hackable. If they do not match it will be very obvious so no need to go character-by-character.
First, for something like the Ledger Nano S, you must install software on your computer anyway to interact with the hardware wallet so it does not offer any convenience advantage over a software wallet like Electrum-LTC. Do not take short cuts, and do not underestimate the importance of security. Transferring Ether out of paper wallet Ask Question. Loading playlists Log into your account. That is all. Ameer Rosic 2 years ago. We are focused on how to do this on Mac OS X, but if there is interest in a write-up for Windows or Linux, please send me an email and let me know. Then you should get it tattooed on your chest, right? Sign up using Email and Password. Hot Network Questions. You will be prompted to select Bitcoin or Bitcoin cash. Hardware wallets are more superior in terms of security of your bitcoins and also more user-friendly than paper wallets. Create an account. The least secure are undoubtedly those hosted on Exchange sites. Move Comment. But there are two main reasons why I do not use hardware wallets. Skip navigation.

Desktop or mobile wallets are also popular choices for a hot wallet. A security-conscious reader may realize that the checksum file itself may have been tampered with, which is why the above steps are not foolproof. Sign in to add this video to a playlist. One cannot send BTC directly from a paper wallet to Ledger as of now. First, you must be absolutely sure when you generate the paper wallet that your computer or the software you are using to generate the paper wallet has not been compromised. In , Mt. You should use at least two different techniques to save and store your private keys. Crypto Bobby , views. Here are the detailed reasons why to do so: Think of it like a fingerprint. Crypto-Bit Brothers 14, views. Share via. But the problem is, they get stuck when they try to migrate because there is no direct way to do so.