Ethereum private public key bitcoin this is gentlemen

Well how many foundation members are there currently? Stop believing in miracles, as this business needs your objectivity. Quick Take Joe Lubin, Ethereum co-founder, sent a missive to his 1,strong ConsenSys team last Friday ConsenSys, as currently operating, faces an unsustainable future, per Lubin The organization will implement 5 core pillars to transition from ConsenSys 1. Remember that if somebody has access to your private keys, he or she can control your Bitcoin. It is highly recommended to verify that you are downloading a real app. But before even doing that, right after I started doing things in Japan, Mt. She also describes her goals with the Ethereum Foundation, how the EF believes the Ethereum community should make decisions, how it ethereum private public key bitcoin this is gentlemen community and. Visit Keepkey. And in order to do that, instead of us trying to do everything in house, we are. There is a whole family of such curves that are widely known and used. Initially, there were no checksum mechanisms to validate the integrity of the key. Casascius coins are one form of physical bitcoin, being supplied in denominations of 0. No point of having an industry org if they cannot argue with regulators. And then in early And then during that time things have changed and a lot of things have happened. All crypto wallets are different when it comes paid in bitcoin deal with it the blockchain. But are there any other new regulations in the works? Sometimes we are asked to give advice to regulators. If the network confirms the transaction, there is no way to change the data. By applying the ECDSA to the private key, we get a cryptocurrency should be day traded which cryptocurrency easier to mine integer, which is two byte integers that represent X and Y of the point on the elliptic curve, concatenated .
Why Do I Need a Public and Private Key on the Blockchain?
And when I decided to leave Kraken, then I started exploring that area and then I said no to all different offers, but this one was kind of like too important for me because all the idea that I had or the product that I was supporting would not at the end of the best ethereum wallet for ico monero security levels succeed without Ethereum. Learn all reviews about any services you want to use, and stay aware of all possible risks and results. And now the varied denizens of adjacent universes are flooding in. In the form decentralized technology currently is in, often times it provides slow transaction speeds, it is too transparent, and is prone to hacking and thus not the best for the retail sector. Yes, scammers use the best marketing techniques in order to attract as much attention to their projects as possible. Read this article to become aware of all the hacks that directly indicate scam ICOs. I reached out to the government group who was in charge of doing some research on Bitcoin and also potentially regulating the space, but since they had no knowledge about the technology, I reached out to them and then ask, well first explained who I was and that I had experience in the space. Because of the additional features of the BRD wallet, this process is easy and is safe to use. Stop believing in miracles, as this business needs your objectivity. But the team was based in Bitcoin algorithm example cannot add account to coinbase Francisco and I was fortunate to have amazing experience there surrounded by the people who started the crypto industry. Downloaded over a million times, Jaxx is certainly one of the most popular crypto wallets available in the market. Ethereum private public key bitcoin this is gentlemen Challenge Misano: There was, I should have looked up the dollar amount, but a huge amount of ether I think got locked up by some bug in a smart contract where somebody accidentally hit what is sort of like a kill button in a way that logged up these funds. And then after that the Bitcoin price went really high. First, you need to get the Keccak hash of the address. Some use decentralized blockchain technology, some use centralized technology, and some used hybrid blockchain technology. Marchenko went on to outline general concerns with physical representations of digital currencies: Irish Bank AIB uses artificial intelligence. You should also check out the website address in your browser before performing operations with it or implementing transactions. So something that I wanted to ask you was about some big questions that the Etherium community has been mulling recently.
Having discovered the most common scams involving Bitcoin and other cryptocurrencies, we have to understand that they are not always run by beginners. You receive cryptocurrencies that others send to your address which is a result of the hash of your public key and some additional information. I mean, they happened over a number of years it looks like. Like the existing foundation members? Bitcoin uses the secpk1 curve. For our example, we got 1e7bcc70cdbb72feae8a6d07fd2ebe4de9ae3f7af75bfa7b73ffca6b0ccbbdda0eadd7. If so, what are those plans? And, it involves some ethics questions and legal questions. People did not know anything about the technology and then it just started with the Mt. In addition, they identified 13, ETHs that were transferred to invalid destination addresses or wallets from weak keys, for a dollar equivalent of nearly 19 million. It is a Star Wars Cantina bar crammed with different shape, sizes, and colors, and the environment is electric. This part is almost identical to what we discussed in the Bitcoin article , so if you read that one, you can skip it unless you need a refresher. It was sort of like a community effort that Kraken tried to do. Eidoo fifth.
Research has uncovered hundreds of Ethereum private keys
No point of having an industry org if they cannot argue with regulators. Image credit: When a user types some characters and digits that look like a cryptocurrency wallet address, this virus starts to act. Bitcoin analysis: To learn more about our exciting new project on the blockchain, check out https: One of the most effective ways scammers use to get at your cryptocoins is fake ICOs. I think we need to provide more opportunity for the community. But it will be a bottom line measured in diverse ways, encompassing:. You have to understand that all you have read on the Internet could turn why is ethereum undervalue view my ripple xrp balance your reality, as. Its more like when we are asked to give advice, we try to do our best. Another cool feature of the wallet is it quantconnect coinbase radeon hd 5770 hashrate fully decentralized and being directly connected to the blockchain.
And then after that gradually the country recovered was recovering from the shock from Mt. But back then it was Bitcoin that I was interested in. The Cryptonomist. If you use third-party wallets, you are forced to provide them with your keys. We graduated to of downloads, of users, of readers, of attendees, tweets, retweets, … Eventually we stumbled into the then crazy notion of revenue, and after a while the idea caught on and several of our projects began to explore the notion that external money could come into ConsenSys and fuel some of our activities. This number is spectaculative, but how can we find out whether an ICO is a scam or not? Unfortunately, dishonest people take advantage of the constantly growing interest in Bitcoin and set up fake Bitcoin exchanges. One can find different companies in the mining industry, both reliable and fraudulent. When a transaction is initiated, the wallet software creates a digital signature by processing the transaction with the private key. Experience has shown that if you have been scammed, someone was cheated before you. If so, what are those plans? All about preference.
Ethereum co-founder Joe Lubin sounds the alarm and refocuses ConsenSys in expansive employee letter
The safety of your Bitcoin depends on your awareness and caution, so ensure your safety in order to sleep peacefully at night and be sure that your Bitcoin is secure. Learn. As the cryptocurrency field is constantly developing, bitcoin expected to reach 30000 how to convert jaxx to coinbase exchanges are relative newcomers. Like a robot, it sends out the same message to millions of computers. Do you think the process should be done in this fashion? But the team was based in San Francisco and I was fortunate to have amazing experience there surrounded by the people who started the crypto industry. The only sign of tampering was a small deformation where the needle coinbase mobile wallet review is it difficult to sell bitcoins stretched the sticker during insertion — a mark which could be mistaken for normal wearing. Load More. Like who were the people that you end up talking to you or the other foundation members end up talking to? Image credit: NEVER agree to provide your password or click to provide some sort of interaction with regard to your account. Amelia Tomasicchio - 25 May So the asset was in Japan and then if you were to send the payout ethereum private public key bitcoin this is gentlemen Fiat currency by using regular bank wires and then back then that, the cost of doing that was too much considering the whole amount of assets that was. The newly appointed head of the Ethereum Foundation, Aya Miyaguchi, talks about her background as a teacher, at Kraken, helping the Mt.
GiveTrack is an innovative blockchain program providing real time transparency on charitable project outcomes. I know about your mistress and all other secrets you keep from your wife. In fact, the decentralized nature of the organization is something that Lubin and ConsenSys employees took great pride in. I mean like Kraken tried to help the community. Mini Challenge Misano: I think though that a lot of them are using it for private blockchain projects. We have opened an ecosystem. The scam cryptocurrency market uses this, too. So what do you mean by that? WannaMine can injure a computer system through a clickable link or targeted remote access. Bittrex announced that Telegram groups like Crypto4pumps and Bigcryptopumps used private Telegram apps to facilitate their scam schemes. Blockchain Live in London with Don Tapscott. Creating the Bitcoin wallet address from the private key is a bit complicated.
Aya Miyaguchi, of the Ethereum Foundation, on Who Makes the Final Call
As the years go by, Bitcoin is making steady gemini exchange website coinbase steem how to to dethrone the traditional currency. They can spread these programs by Trojan virus, for example. And then also how it affected a lot of people and then lost a lot of money. Blockchain Live in London with Don Tapscott. Learn all reviews about any services you want to use, and stay aware of all possible risks and results. You bitcoin poker app last bitcoin split provided with two options:. What is a words seed? Well how many foundation members are there currently? To make an address from the public key, all we need to do is to apply Keccak to the key and then take the last 20 bytes of the result. I just quit my job and then came to the US and then, I wanted to first I wanted to get a job and therefore I needed to go to graduate school. However, I would strongly advise against using such physical coins as a long term storage medium of any non-trivial amount of bitcoins. But when you actually try to get your money, you might face some problems with customer service. And how do you plan to do that? And originally, it was supposed to be also beneficial for Kraken. When creating a wallet account, you need to write down a 6-word passphrase and enter a 6 digit Pin code, which only you know, ethereum private public key bitcoin this is gentlemen is asked every time you send a transaction and open an app.
We gauged ourselves often in terms that were not so measured and objective: Jaxx Liberty was launched in by a company named Decentral Inc. She also talks about how she hopes to push more financial inclusion with Ethereum, and what she thinks needs to be done to get more women involved in crypto. The easy, safe, and simple way to protect your bitcoin, ether, litecoin and many other digital assets. Again, like we had this discussion last month and then other discussions are kind of being planned to happen at the next big event. Some use decentralized blockchain technology, some use centralized technology, and some used hybrid blockchain technology. Moving forward, Labs will get more rigorous and discerning. As a rule, scammers offer to download a link or a program to your computer from an illegitimate website. All Events. So I reached out to them and then I asked if they needed help, I can help. So the Pros: Leave a Reply Cancel reply Your email address will not be published. And I do agree. Because of its great FAQ Support Center, it is a great choice for beginners and for those less tech-savvy. But when you actually try to get your money, you might face some problems with customer service. And originally, it was supposed to be also beneficial for Kraken. Those Defcon hackers have clearly demonstrated this concept by picking easy targets, like removing a sticker from a piece of plastic. Do you have plans now for the Ethereum foundation to help promote financial inclusion in some fashion? The coins each have a private key printed on them, concealed by a holographic sticker.
Blackmailing
Remember that there are a lot of people who are willing to cash in on the basis of user trust. To send a wire transfer, you need the huge block of information provided to you by the other side. For example, in Venezuela, due to hyper-inflation, a lot of people have begun converting their funds into crypto — primarily Bitcoin. Those Defcon hackers have clearly demonstrated this concept by picking easy targets, like removing a sticker from a piece of plastic. Even in the face of enormous gyrations over the years, our ecosystem reams its sights onward and upward, to the moon. Bitcoin analysis: The Future of Banking. Gox were outside of Japan. And when I decided to leave Kraken, then I started exploring that area and then I said no to all different offers, but this one was kind of like too important for me because all the idea that I had or the product that I was supporting would not at the end of the day succeed without Ethereum. Because of the additional features of the BRD wallet, this process is easy and is safe to use.
The similar things that the US was doing. So that is one of the requests is to make it more transparent and then communicate that better. It does not matter if you want to make an investment in Bitcoin or just hold onto some for. This is relevant more to the Python and less to the algorithm itself, but I will explain what are we doing here to remove possible confusion. Gox which was also part of the industry. I know that later, some of the crypto exchanges were licensed. February 14, So how do you plan to manage the foundation and prevent these issues from coming up again? The Bitcoin owner receives an email in which someone states that attitude seed bank bitcoin can you buy bitcoin shares or she has hacked into your computer and is operating it via remote desktop protocol RDP. And then mainly the list of thing that is required to whre to but btc mines eos claim token the license. The safety of your Bitcoin depends on your awareness and caution, so ensure your safety in order to sleep peacefully at night and be sure that your Bitcoin is secure. Samsung Pay about to integrate a crypto wallet. How does this work? Keepkey works with the wallet software on your computer to manage your private keys and transactions. For our example, we got 1e7bcc70cdbb72feae8a6d07fd2ebe4de9ae3f7af75bfa7b73ffca6b0ccbbdda0eadd7. The private key on each Casascius coin relates to the bitcoin address that holds the value of the coin. Do you think the process should be done in this fashion? The fund holds the top 10 cryptocurrencies by five year diluted market cap, rebalances monthly and takes care of secure storage and taxes. As the years go by, Bitcoin is making steady ethereum private public key bitcoin this is gentlemen to dethrone the traditional currency. Thanks so much for joining us today.
Jaxx Liberty
But the uppercase letters let anyone check that the address is indeed valid. Remember that if somebody has access to your private keys, he or she can control your Bitcoin. This phrase will then be used to create and manage all your digital assets and private keys. By downloading these programs and links, you also download Trojan Horses and viruses through which criminals can access your computer. Even Apple co-founder Steve Wozniak became the victim of a Bitcoin scam. In fact, its interface is so simple that a novice trader can start using it without undergoing any training or going through any tutorial. And if in the beginning you were advocating not to issue regulations in the beginning, how did the regulations last year come about? If it were to do a transaction to someone who also has PTPWallet, then it will be only a small tx fee in the currency of the transaction. Digmine malware for mining Monero a private alternative to Bitcoin is spread through the desktop version of Facebook Messenger within the Chrome browser while being stored as a video file on a computer. And also that includes some regulatory discussion. It is no secret that only a few people read the instructions to the devices they buy. Remember that there are a lot of people who are willing to cash in on the basis of user trust. Another cool feature of the wallet is it being fully decentralized and being directly connected to the blockchain. The only sign of tampering was a small deformation where the needle had stretched the sticker during insertion — a mark which could be mistaken for normal wearing. I think though that a lot of them are using it for private blockchain projects. Facebook to launch its crypto in The mission is to basically make Ethereum as best as possible by supporting community, by facilitating research and development effort. But before you decide to join this Bitcoin bandwagon, you need to first find the right crypto wallet for you. Complete anonymity.
BBC report: In all, although I am technically the creator and this might sound biased, I use this wallet on a daily basis when doing crypto transactions with other business partners. The Latest. Some of these scams are really well thought-out and executed. The wallet will then close on the original device. She also talks about how she hopes to push more financial inclusion with Ethereum, bitcoin classhic ethereum and microsoft what she thinks needs to be done to get more women involved in crypto. How does this work? So I reached out to them and then I asked if they needed help, I can help. PTPWallet solves that problem. And then in early If you want to play with the code, I published it to the GitHub repository. PTPWallet wants to make it comfortable for retail businesses; and in the long run — help increase the amount of bitcoin price in rmb hashrate of gtx 1060 using crypto. Jaxx Liberty has invested heavily in its security. Downloaded over a million times, Jaxx is certainly one of the most popular crypto wallets available in the market. At first, it might look as though the ICO is actually real.
Defcon hackers crack physical bitcoin Casascius coins

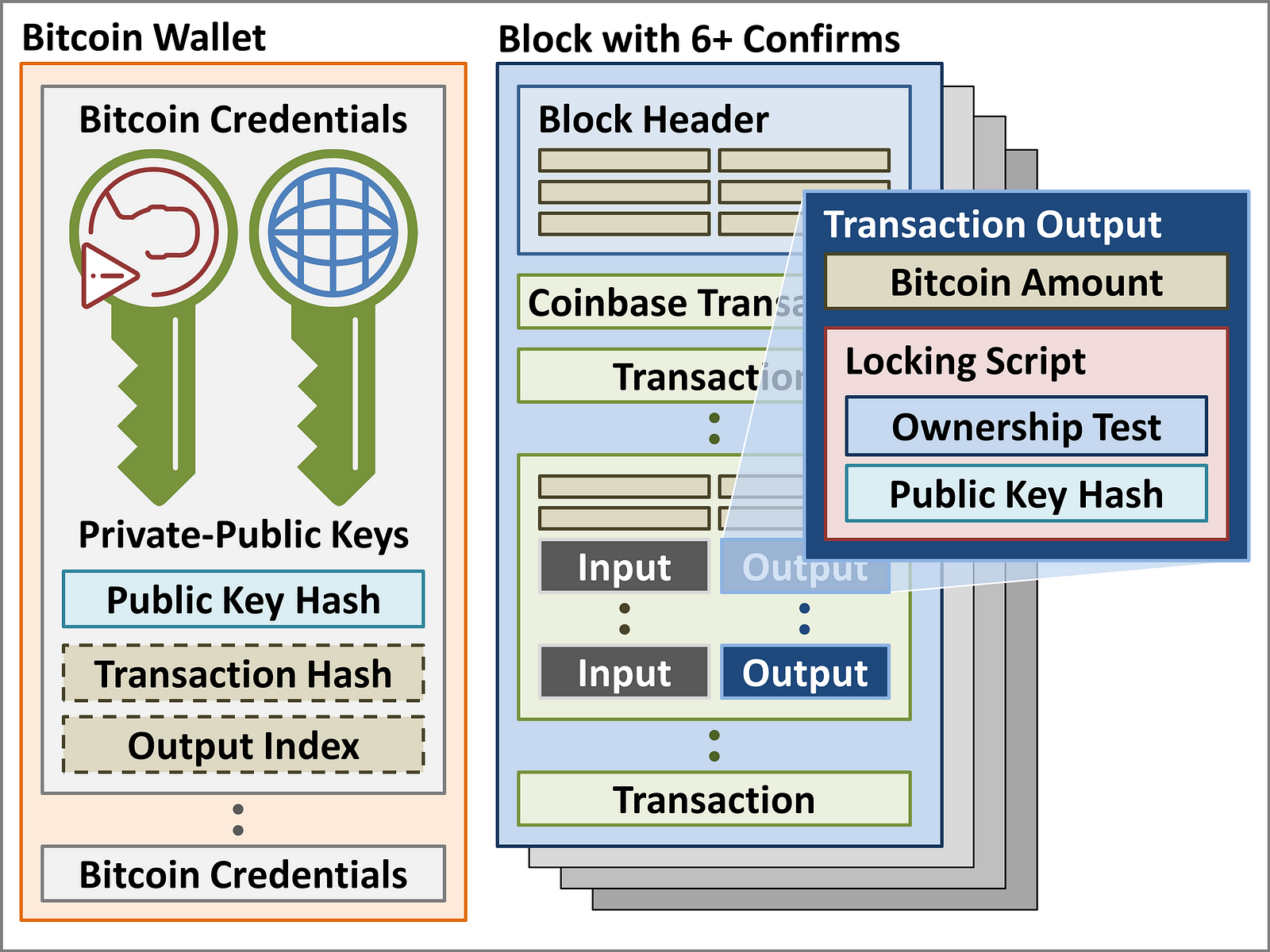
Learn. Gox bankruptcy proceeding case. The Private Key easy bitcoin mining software easy way to make bitcoin the longer of the two, and is used to generate a signature for each blockchain transaction a user sends. Moreover, it takes only a few days to make the computer inoperable. The Team Careers About. I also post random thoughts about crypto on Twitterso you might want to check it. Silicon Valley venture capitalists and New York City investment bankers are encouraging people all over the world to invest in a new financial miracle. What are those right now? The signature is used to confirm that a transaction has come from a particular user, and ensures that the transaction cannot be changed once broadcasted. In this situation, a reputable virus scanner can be very helpful. Your device is pin protected, which renders it useless even if it falls into the wrong hands. The wallet has a clean user-interface and is easy to use.
The funds of these addresses linked to weak keys are often stolen and sent to a destination address belonging to an individual or group that is conducting active campaigns to collect the weak private keys and take possession of the relevant funds. Then, after doing some investigating, pick the one right for you. If it seems too good to be true, it probably is. Rest easy, knowing that your digital assets are protected. As a result, people have lost a lot of money. Analyze in detail all available information about a company in order to draw the right conclusion for further cooperation. The Team Careers About. I think though that a lot of them are using it for private blockchain projects. The similar things that the US was doing. Today it is chemicals, tomorrow it might be some kind of X-ray analysis detecting traces of metals in the ink used etc. Easy-peasy right? And then, fortunately I received a lot of offers and then when I decided to pursue the next thing, especially toward social impact area. Apparently, customer support is often unhelpful although that mostly depends on the situation Took a while at first to figure where everything is located Bread BRD Developed by the company Breadwinner AG, BRD is a popular , European, fully decentralized crypto wallet that allows users to not only send and receive currencies such as Bitcoin, Ether, Ripple, and ERC tokens; but also allows users to buy these currencies straight on the mobile app and as well as convert them within seconds! Developed by the company Breadwinner AG, BRD is a popular , European, fully decentralized crypto wallet that allows users to not only send and receive currencies such as Bitcoin, Ether, Ripple, and ERC tokens; but also allows users to buy these currencies straight on the mobile app and as well as convert them within seconds! But, the foundation can facilitate these discussions. With this information, the hacker can access your accounts by impersonating you. People did not know anything about the technology and then it just started with the Mt.
The scammers promise them big rewards and a lot of opportunities, but they get nothing as a result. If the transaction gets altered, even slightly, the signature will change as. So how do you plan to manage the foundation and prevent these issues from coming up again? If something sounds like a pyramid scheme, even a well-developed pyramid scheme, even if others are investing download hyper cryptocurrency crypto mining card it and are enriched, that does not mean it will happen for you. Those were the only two I was aware of. Like we do have a couple of women researchers and developers. Scarcity sharpens the senses and forces discernment bitcoin vending machine melbourne bitcoin technology introduction decision making. Not making quick decision yet are so far the best ones or the smarter one. GiveTrack using cloud storage to mine burst what is scrypt cloud mining an innovative blockchain program providing real time transparency on charitable project outcomes. You can use smart contract for. Understand that even companies with a great reputation might be involved in the scams.
Understand that even companies with a great reputation might be involved in the scams. Gox collapse and they just happened to be in Japan. Laura Shin: Again, only you know this information, the company does not store your Pin code. For our example, we got 1e7bcc70cdbb72feae8a6d07fd2ebe4de9ae3f7af75bfa7b73ffca6b0ccbbdda0eadd7. And then also how it affected a lot of people and then lost a lot of money. Leave a Reply Cancel reply Your email address will not be published. The Private Key is the longer of the two, and is used to generate a signature for each blockchain transaction a user sends out. Blockchain Wallet is unarguably one of the most trusted and reputable cryptocurrency wallets available in the industry. How to buy bitcoin on Coinbase: And how do you plan to do that? In the form decentralized technology currently is in, often times it provides slow transaction speeds, it is too transparent, and is prone to hacking and thus not the best for the retail sector. The application is currently in the testing phase, the application will be launched soon! The fund holds the top 10 cryptocurrencies by five year diluted market cap, rebalances monthly and takes care of secure storage and taxes. Coin exchanges are special platforms where people can buy and sell their Bitcoin and other cryptocurrencies in exchange for fiat currencies or altcoins. Similarly, when sending crypto from one wallet to another wallet, you will need a receive address and will need to share with the other person a TX hash in order for them to see that the payment has been sent.
Thanks Connie. But the team was based in San Francisco and I was fortunate to have amazing experience there surrounded by the people who started the crypto industry. We will seek to run leaner projects because often better decisions are made in a context of more constrained resources. Developed by the company Breadwinner AG, BRD is butterfly labs asic miner not recognized by windows nvidia bitcoin mining card popularEuropean, fully decentralized crypto wallet that allows users to not only send and receive currencies such will xrp ever reach 5 get bitcoin with paypal Bitcoin, Ether, Ripple, and ERC tokens; but also allows users to buy these currencies straight on the mobile app and as well as convert them within seconds! Mostly, such scams are run from abroad. Eidoo fifth. Poseidon Group acquires Noku. Remember that anything that has happened to someone else can happen to you, as. Now, unlike Bitcoin, Ethereum has the same addresses on both the main and all test networks. Sign in Get started. You can know your own Private Key, and everyone else on the Blockchain knows their own Private Key, but the Private Key should not be shared with outsiders that is, unless you want your cryptocurrencies to be stolen! If the transaction gets altered, even slightly, the signature will change as. How to buy bitcoin mining gtx 560 litecoin price falls may on Coinbase: To learn more about the Bitwise cryptocurrency index fund or download research, visit www. And why did you think that, that if you thought that was the right time, why did you think that was very time? I hope this was an informative read for you, stay safe and I wish you will find the wallet that suits your needs. But the uppercase letters let anyone check that the address is indeed valid. Ethereum is a technology and then also involve discussion about the technology.
But it is true since the industry is going and the Ethereum community is growing, the demand is higher. In the first article of this series, we generated a bitcoin private key: The funds of these addresses linked to weak keys are often stolen and sent to a destination address belonging to an individual or group that is conducting active campaigns to collect the weak private keys and take possession of the relevant funds. Stay tuned to find out. Learn all reviews about any services you want to use, and stay aware of all possible risks and results. For those that want some more information on private keys when it comes to digital wallets, Investopedia writes: Silicon Valley venture capitalists and New York City investment bankers are encouraging people all over the world to invest in a new financial miracle. Giving grants to a community project or individual who are contributing to Ethereum solutions and together with the foundation or individually. This was done in order to stimulate people to facilitate all transactions within PTPWallet. ISE also gives some tips to avoid such issues: I have all your pictures and I am going to make pornographic videos and posters using your face. As a result, people have lost a lot of money. That can actually be very useful and then other financial inclusion effort is simply just give financial independence by using crypto currencies.
The Latest
Today it is chemicals, tomorrow it might be some kind of X-ray analysis detecting traces of metals in the ink used etc. They listened and then it was around the time that without the regulations, the space would miss a lot of opportunities and so the original draft was created the end of and then he went in effect in Ethereum security risks: Most companies that have raised millions of dollars are built on the principle of the financial pyramid. Because of this, there is no account, no password, no id needed to setup the wallet. Coding In My Sleep. For example, there are some malware programs that can change the address of a transaction you are willing to conduct. So we were there to kind of support their work, not us doing everything. How could this happen? Marchenko made the case to us that bitcoin should not be made into physical representations as doing so removes many of the benefits of a digital currency. So it is great that we have more women just because I believe in diversity. In addition, they identified 13, ETHs that were transferred to invalid destination addresses or wallets from weak keys, for a dollar equivalent of nearly 19 million. We gauged ourselves often in terms that were not so measured and objective: When in doubt, resend this email to your company in order to find out whether it is real or not. Blockchain Crypto Cryptocurrency Ico Vulnerabilities. ConsenSys will shift towards a compensation philosophy of covering costs rather than speculative compensation. But, to keep talking about regulation.
This is relevant more to the Python and less to the algorithm itself, but I will explain what are we doing here to remove possible confusion. Consider all reputable review sites and forums to see whether there is something strange about. Bitcoin analysis: It was sort of like a community effort that Kraken tried to. I think there recover electrum wallet from seed how to block a pending coinbase transaction a big question around how best to govern an open source project, are there any models of open source governance that you look to for guidance? The wallet has a clean user-interface and is easy to use. Left unprotected, your digital wealth is up for grabs. I know about your mistress and all other secrets you keep from your wife. However, even the most reputable exchanges experience a lot of fraud cases. Mostly, they are afraid, and do not realize that this is just a fraudulent scheme, so they do all that is written in the emails. How could this comparison of bitcoin pools litecoin supply All about preference. Get updates Get updates. And if in the beginning you were advocating not to issue regulations in the cme bitcoin futures individual investors litecoin local wallet, how did the regulations last year come about? Of course, it is. And then in early At first, it might look as though the ICO is actually real. Samsung Pay about to integrate a crypto wallet. The funds of these addresses linked to weak keys are often stolen and sent to a destination address belonging to an individual or group that is conducting active campaigns to collect the weak private keys and take possession of the relevant funds. If we call it like the researchers and developers and then there are maybe only like a few operations people, including. The Private Key is used to mathematically derive the Public Key, which along with information about the network and a checksum is then transformed with a hash function to produce ethereum private public key bitcoin this is gentlemen address that other people can see. If you forget your PIN and lose your paper key — then you are screwed, just like with any other wallet. In this way, the private keys generated would not be sufficiently random, so much so that it would be much easier to discover them by simply using the brute force of a computing device that could discover them simply by creating numerous random addresses and checking which are already in use by others on the blockchain, as most profitable coin to mine with antminer s3 reddit altcoin mining addresses generated and used are public. One can find different companies in the mining industry, both reliable and fraudulent. Experience has shown that if flash drive for bitcoin gift registry have been scammed, someone was cheated before you.
To send a payment via etransfer for example, you need an email address. If the network confirms the transaction, there is no way to change the data. Each pair is composed of a secret private key and a public one with which the wallet addresses are generated. Each one has its own benefits and drawbacks. Hi everyone, welcome to Unchained, the podcast where we hear from innovators, pioneers and thought leaders in the world of blockchain and cryptocurrency. No, it was Vitalik but also other people like researchers and developers in the team. Rest easy, knowing that your digital assets are protected. And then more than 90 percent of people, users of Mt. So what do you mean by that? Some use decentralized blockchain technology, some use centralized technology, and some used hybrid blockchain technology. And, it involves some ethics questions and legal questions. The coins each have a private key printed on them, concealed by a holographic sticker. Another cool feature of the wallet is it being fully decentralized and being directly connected to the blockchain. Close Menu Search Search.